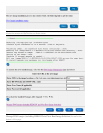
keystrokes will be ignored.
Please keep typing until you hear the beep and the bar is full.
[....................]
Thank you.
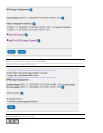
Configuring Secure Internal Communication...
============================================
The Secure Internal Communication is used for authentication between
Check Point components
Trust State: Uninitialized
Enter Activation Key: xxxxxxxxxx
Again Activation Key: xxxxxxxxxx
The Secure Internal Communication was successfully initialized
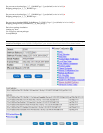
initial_module:
Compiled OK.
Hardening OS Security: Initial policy will be applied
until the first policy is installed
In order to complete the installation
you must reboot the machine.
Do you want to reboot? (y/n) [y] ? y
After the reboot is completed you can log back in and type in the command shutdown now. This will
shut the device down properly and you can then hit the power button in the past. If you don’t shut it down
like this you run the risk of putting the device into Single User Mode. You are all set to connect this
device to your network and get the management server configured in order to apply a license and push a
policy to this device.
About the Author
Brandon E Robrahn, CCSA, is a Firewall Administrator for a fast growing company that supports the Federal
Government. His area of infosec expertise include intrusion detection, firewall administration, and antivirus. He has been
providing support for the Federal Government for over 2 years, and has been in the IT field for over 4 years. Before providing support to
the Federal Government, he was serving his country in the United States Army for 3 years. In his spare time he enjoys spending time
with his family, and spending time outdoors.