ZENworks® ESM 3.5 Administrator’s Manual 128
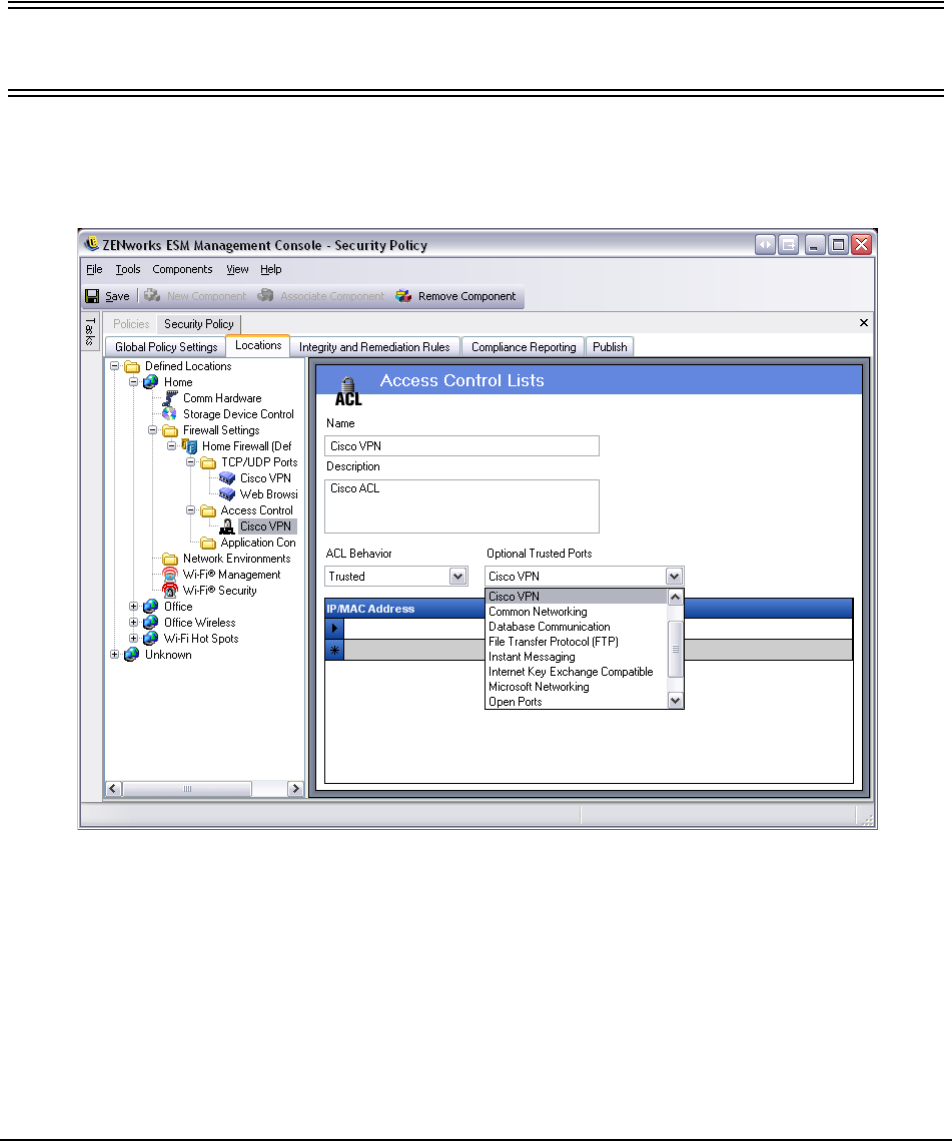
Access Control Lists
There may be some addresses which require unsolicited traffic be passed regardless of the current
port behavior (i.e., enterprise back-up server, exchange server, etc.). In instances where
unsolicited traffic needs to be passed to and from trusted servers, an Access Control List (ACL)
can be created to resolve this issue.
Note:
This feature is only available in the ESM installation, and cannot be used for UWS security policies.
To access this control, open the Locations tab, click the “+” symbol next to Firewall Settings,
click the “+” symbol next to the desired Firewall, and click the Access Control Lists icon in the
policy tree on the left.
Figure 92 : Access Control Lists Settings
To create a new ACL setting:
Step 1: Select Access Control List from the components tree and click the Add New button
Step 2: Name the ACL and provide a description
Step 3: Enter the ACL address or Macro
Step 4: Enter the ACL type:
