Nokia Network Voyager for IPSO 4.0 Reference Guide 225
VPN but not want to route unencrypted traffic through the cluster. For this purpose, you can use
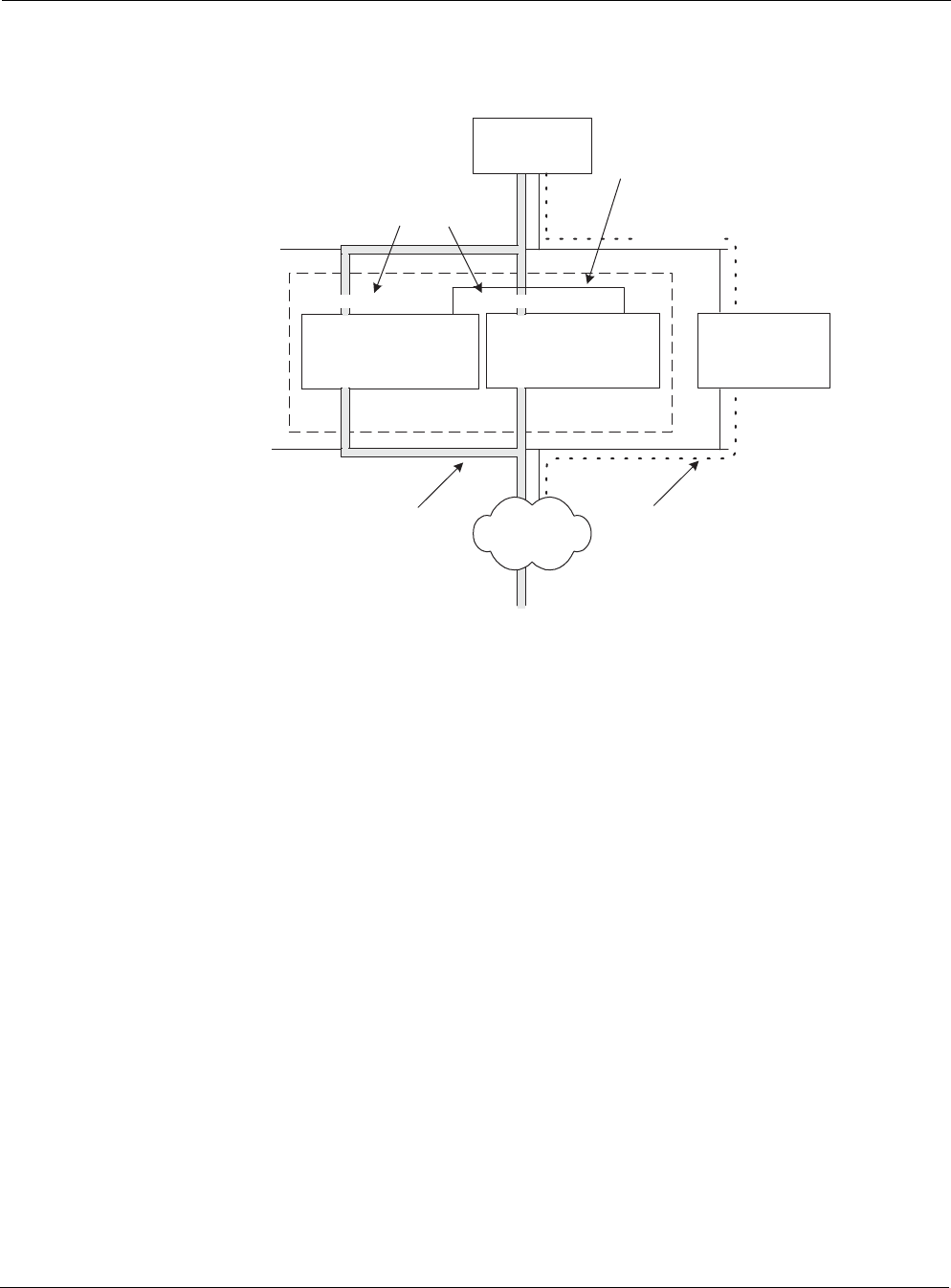
a configuration similar to the one shown in the following diagram:
The purpose of this configuration would be to route the outgoing unencrypted traffic through the
default gateway and route the outgoing encrypted traffic through the cluster. Traffic that passes
through the cluster is NATed so that the source address of a packet is translated to one of the
addresses in the IP pool of the cluster node that handles the connection.
How you configure IP pools depends on whether a non-Check Point gateway participates in the
VPN:
If the other end of the tunnel is also a Check Point gateway, you do not need to configure the
IP pools in IPSO. Simply follow the instructions in “Using IP Pools When Only Check Point
Gateways Are Involved.”
If the other end of the tunnel is not a Check Point gateway, you must follow the instructions
in “Using IP Pools When Only Check Point Gateways Are Involved” and also configure the
IP pools in IPSO, as explained in “Configuring IP pools in Cluster Voyager.”
Using IP Pools When Only Check Point Gateways Are Involved
To set up the configuration shown in the previous diagram, you would:
Configure the IP pools in NGX.
On the internal router:
create a default route to the Internet with 192.168.1.1 (the default gateway) as the
gateway address.
create static routes to the IP pool networks with the internal cluster IP address
(192.168.1.10) as the gateway address. Do not use the real IP addresses of the internal
VPN Traffic
Firewall A
IP Pool: 10.1.2.0/24
Firewall B
IP Pool: 10.1.3.0/24
Internal Cluster IP
Address
192.168.1.3
192.168.1.2
Primary Cluster Protocol
Network 192.168.3.0
192.168.3.1
192.168.3.2
Internal
Router
192.168.1.10 192.168.1.10
Internet
Default Gateway
192.168.1.1
192.168.1.0
Unencrypted Traffic


















