Nokia Network Voyager for IPSO 4.0 Reference Guide 411
Caution
Enabling multihop BGP connections is dangerous because BGP speakers might
establish a BGP connection through a third-party AS. This can violate policy
considerations and introduce forwarding loops.
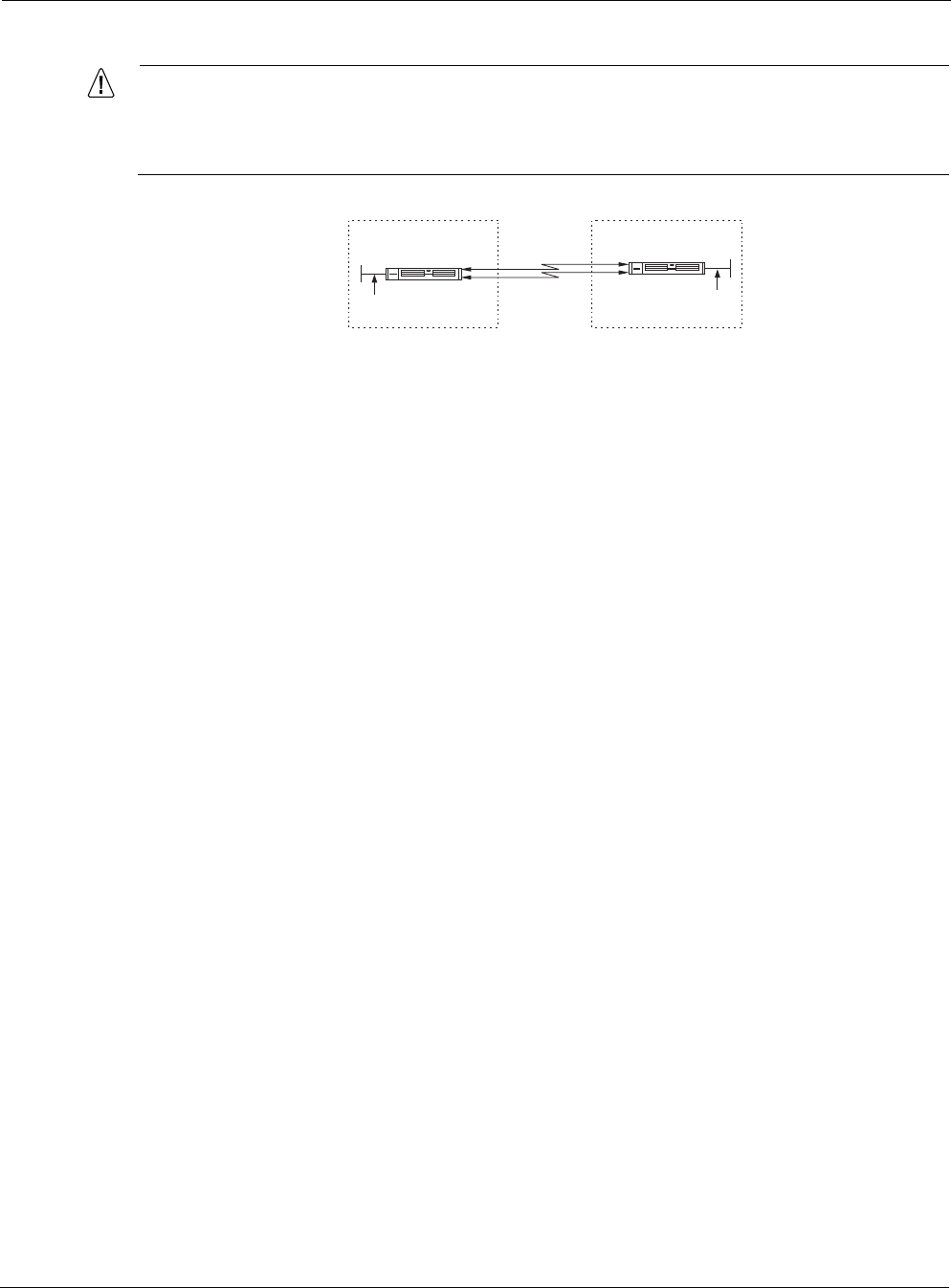
Router A and Router B are connected by two parallel serial links. To provide fault tolerance and
enable load-balance, enable EBGP multihop and using addresses on the loopback interface for
the EBGP peering sessions.
Route Dampening
Route dampening lessens the propagation of flapping routes. A flapping route is a route that
repeatedly becomes available then unavailable. Without route dampening, autonomous systems
continually send advertisement and withdrawal messages each time the flapping route becomes
available or unavailable. As the Internet has grown, the number of announcements per second
has grown as well and caused performance problems within the routers.
Route dampening enables routers to keep a history of the routes that are flapping and prevent
them from consuming significant network bandwidth. This is achieved by measuring how often
a given route becomes available and then unavailable. When a set threshold is reached, that route
is no longer considered valid, and is no longer propagated for a given period of time, usually
about 30 minutes. If a route continues to flap even after the threshold is reached, the time out
period for that route grows in proportion to each additional flap. Once the threshold is reached,
the route is dampened or suppressed. Suppressed routes are added back into the routing table
once the penalty value is decreased and falls below the reuse threshold.
Route dampening can cause connectivity to appear to be lost to the outside world but maintained
on your own network because route dampening is only applied to BGP routes. Because of
increasing load on the backbone network routers, most NSPs (MCI, Sprint, UUNet etc.) have set
up route suppression.
TCP MD5 Authentication
The Internet is vulnerable to attack through its routing protocols and BGP is no exception.
External sources can disrupt communications between BGP peers by breaking their TCP
connection with spoofed RST packets. Internal sources, such as BGP speakers, can inject bogus
routing information from any other legitimate BGP speaker. Bogus information from either
external or internal sources can affect routing behavior over a wide area in the Internet.
AS1
EBGP
00330
Nokia
Platform A
AS2
Nokia
Platform B
Loopback
Address
Loopback
Address


















