Nokia Network Voyager for IPSO 4.0 Reference Guide 329
An encapsulation security payload (ESP) that provides authentication and confidentiality
through symmetric encryption, and an optional anti-replay service. ESP does not include the
IP header in the authentication/confidentiality.
A protocol negotiation and key exchange protocol (IKE) for easier administration and
automatic secure connections. IKE introduces two negotiations. Phase 1 negotiation
authenticates both peers and sets up the security for the Phase 2 negotiation. IPSec traffic
parameters are negotiated in Phase 2.
Transport and Tunnel Modes
The basic building blocks of IPSec, AH and ESP, use symmetric cryptographic techniques for
ensuring data confidentiality and data signatures for authenticating the data’s source. IPSec
operates in two modes:
Transport mode
Tunnel mode
In transport mode the original IP header remains the outer header. The security header is placed
between the IP header and the IP payload. This mode offers some light bandwidth savings, at the
expense of exposing the original IP header to third party elements in the packet path. It is
generally used by hosts—communication endpoints. This mode can be used by routers if they
are acting as communication endpoints.
With IPSec transport mode:
If AH is used, selected portions of the original IP header and the data payload are
authenticated.
If ESP is used, no protection is offered to the IP header, but data payload is authenticated
and can be encrypted.
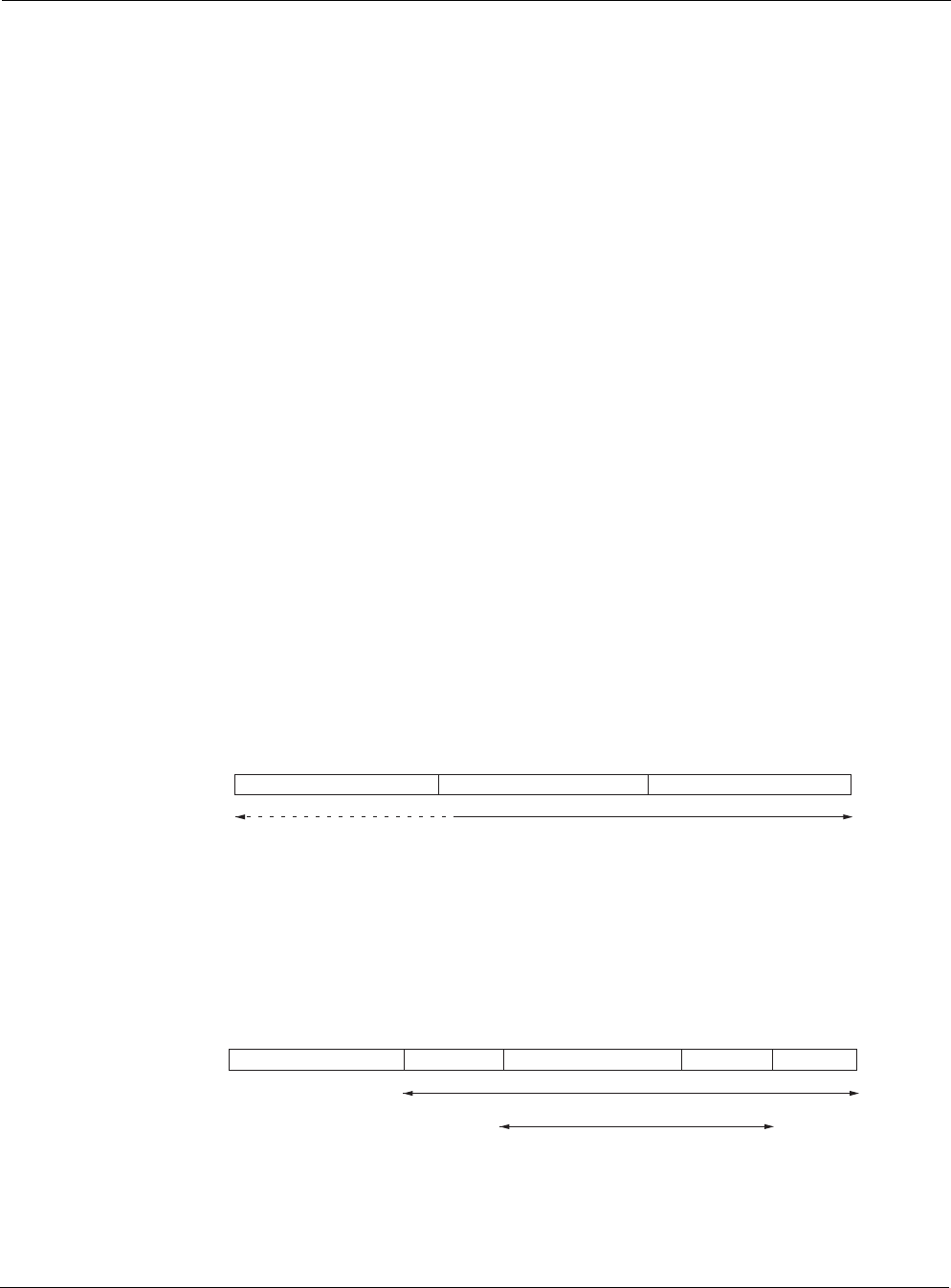
IP header AH Payload
IP header ESP
header
Payload ESP trailer ESP auth
IP header AH
Authenticated
Payload
00126
IP header ESP header Payload ESP trailer ESP auth
Authenticated
Encrypted
00127


















